
If you’ve felt seismic shifts in the European cybersecurity landscape recently, it’s likely due to the arrival of the Network and Information Systems 2 (NIS 2) Directive. Entering into force on January 16, 2023, NIS 2 required EU Member States to transpose it into national law by October 17, 2024. Now, as we find ourselves in mid-November 2024, there is a slight panic in the online space and a definite sense of urgency, with organisations still unclear about what navigating NIS 2 compliance will feel like.
Making matters even more complex, the NIS 2 Directive functions alongside other cybersecurity regulations. It stands alongside other EU cybersecurity regulations, such as the Digital Operational Resilience Act (DORA) and the Cyber Resilience Act. This overlap has left many wondering where each regulation begins, how they intersect, and what NIS 2 brings that’s new.
In this article, we will attempt to demystify the NIS 2 Directive and help you understand better what is new and what you need to know.
Remember, as a Directive, NIS 2 requires each EU Member State to transpose its requirements into national law. This process not only brings new deadlines but also contextual guidelines and specific regulatory bodies that will oversee compliance at the local level. Be sure to check your country’s implementation to ensure it stays aligned with any additional national requirements.
In short, NIS 2 is the second iteration of the EU’s Network and Information Systems Directive. As did its predecessor, it aims at establishing a consistent set of cybersecurity standards across the European Union.
NIS 2 puts a stronger focus on strengthening the cyber resilience of critical infrastructure and essential services, which is not surprising in a geopolitical landscape with state-sponsored cyberattacks increasingly targeting critical infrastructures on the rise. Furthermore, it aims to foster stronger collaboration mechanisms between EU member states to establish a more unified cybersecurity defence front against cyber threats.
At the national level, NIS 2 aims to make sure that each Member State is prepared for cyber threats with a dedicated Computer Security Incident Response Team (CSIRT) and a qualified national authority for network and information systems.
If you are interested in learning more about the evolution from NIS to NIS 2, this infographic by SANS does a good job of visualising the key differences between the two directives.
In any case, one of the most notable changes with NIS 2 is its broadened scope. NIS 2 now applies to a larger range of sectors, dividing them into “essential entities” and “important entities”, as shown in Fig. 1

One thing that differentiates the two categories of entities is also the size of the fines and administrative penalties:
What is more, NIS 2 makes it clear that cybersecurity responsibility extends to top management. In cases of gross negligence, management bodies can now face criminal sanctions, including personal liability.
Besides administrative fines, NIS 2 also grants supervisory bodies the power to order security audits and issue threat notification and compliance orders and binding instructions. NIS 2 also envisages stricter requirements for relevant entities and grants supervisory bodies the right to enforce additional requirements.
On the topic of requirements, there NIS 2 outlines four key areas of compliance and establishes ten baseline cybersecurity measures that covered entities must implement to ensure consistent and effective cybersecurity practices.
The areas of compliance are:
A “significant” incident is defined as one that causes or has the potential to cause major disruption to essential services, financial losses, or severe impacts on other businesses or individuals.
NIS 2 further outlines ten baseline cybersecurity measures that organisations must implement. These practices create a foundation for effective cybersecurity, covering essential risk management, incident response, and data protection processes.
The required measures are:
Together with the four key areas of compliance, they provide a comprehensive framework that empowers organisations to strengthen their defences against an increasingly complex cyber threat landscape.
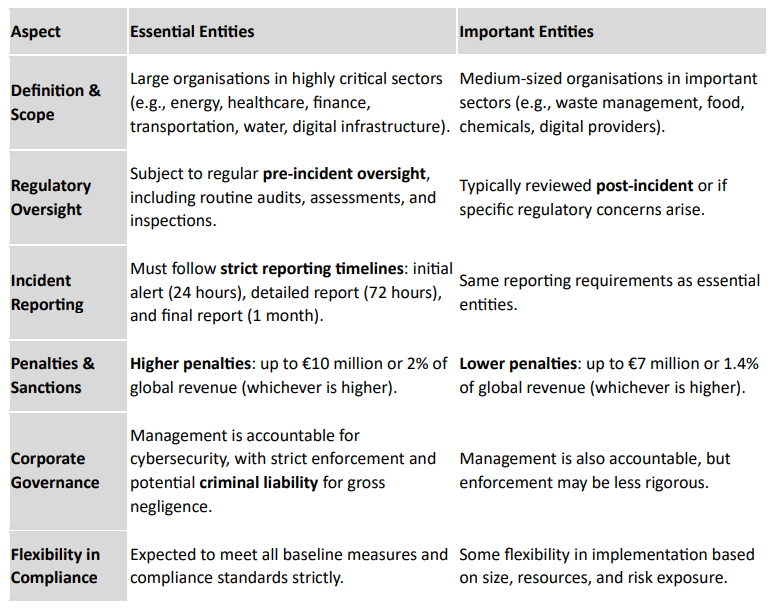
Under the NIS 2 Directive, the requirements for essential and important entities are similar in many respects, but there are some differences in compliance obligations and regulatory scrutiny.
Essential entities are subject to regular oversight and proactive inspections, meaning that regulatory authorities may conduct audits, security assessments, and inspections even if no incident has occurred. Important entities are typically reviewed after an incident or in response to specific concerns raised by regulatory authorities.
Both essential and important entities are required to report significant incidents to authorities and must follow the same incident reporting protocol for significant cybersecurity incidents:
However, essential entities may face additional reporting obligations at the discretion of regulatory authorities, particularly if they operate in sectors with high national security implications.
There are differences in penalties as well, as discussed above. To have a more visual summary of the differences between the requirements for essential and important entities, we have provided a comparative analysis in Table 1 below.
NIS 2 applies to a broad range of organisations that are essential or important to the EU’s infrastructure and economy.
It also impacts non-EU companies providing services within the EU, ensuring that cybersecurity standards are upheld consistently across borders, if the provided services meet the criteria to be classified as essential or important.
Furthermore, non-EU organisations that offer services in multiple EU countries must comply with NIS 2 requirements in each member state where they operate. These non-EU entities must adhere to the same cybersecurity, incident reporting, and risk management requirements as EU-based essential and important entities.
Table 2 below summarises who needs to comply with NIS 2 if providing services within the EU. Regardless of where the organisation is headquartered or if it is headquartered within the EU:

Therefore, most small and micro enterprises are not automatically bound by NIS 2’s primary requirement, so it is possible that NIS 2 would not affect most small businesses that much.
However, certain businesses may still be required to comply if they fulfil a “key role” for society, the economy, or critical sectors. For instance, a small IT service provider that supports critical infrastructure could fall under NIS 2’s scope due to its strategic importance. Member States are required to issue tailored guidelines and provide assistance to small and micro enterprises that fall under the directive. Additionally, each Member State is encouraged to establish resources and points of contact specifically for SMEs, offering direct cybersecurity guidance or referrals to appropriate support services.
Furthermore, NIS 2 emphasises the importance of supply chain security, which can impact small and micro businesses indirectly. What we mean by this is that larger entities that fall under NIS 2 must ensure that their supply chains, including smaller suppliers, meet certain cybersecurity standards. This could lead to situations where small and micro enterprises need to demonstrate a certain level of cybersecurity maturity to maintain business relationships with NIS 2-compliant clients.
As such, while the high compliance thresholds are generally seen as a relief for smaller businesses, without clear support measures, those businesses might struggle to meet the heightened expectations of their larger clients without formal compliance frameworks in place, so be prepared for the need to elevate your cybersecurity efforts in all cases.
As mentioned in the introduction, NIS 2 is not a standalone cybersecurity directive but a part of a broader cybersecurity regulatory framework at the European level, which aims to enhance resilience, trustworthiness, security and technical robustness across various sectors and digital environments.
One such regulation is the Digital Operational Resilience Act (DORA). DORA is specifically designed for the financial sector and addresses information and communication technology (ICT) risk management within financial services. DORA entered into force on 16 January 2023 and will apply as of 17 January 2025 with the goal of ensuring the operational resilience of financial institutions, including banks, insurance companies, and investment firms, against ICT-related risks.
For financial entities, DORA supersedes certain NIS 2 requirements regarding ICT risk management, reporting, and digital resilience. In areas where the two directives overlap, such as risk management and incident reporting, DORA takes precedence for financial institutions. This approach helps avoid duplication of compliance requirements and ensures that financial organisations focus on a tailored set of cybersecurity standards specific to their industry’s unique risk landscape.
Another directive which is important to mention is the Critical Entities Resilience (CER) Directive, which has been in force since December 14, 2022.
While both CER and NIS 2 apply to critical sectors, they cover different aspects of resilience. CER addresses physical and operational risks, such as natural disasters and terrorist attacks, whereas NIS 2 is focused specifically on cybersecurity requirements for the same sectors. Organisations in critical sectors will need to comply with both CER for non-cyber risks and NIS 2 for cybersecurity.
Of course, we also need to mention the Cyber Resilience Act (CRA), which was adopted by the Council on October 10, 2024, with reporting obligations expected to go into effect around mid-2026 and the beginning of 2027. The CRA targets the cybersecurity of digital products and connected devices within the EU. It sets security requirements for hardware and software products with digital elements, ensuring they are designed with cybersecurity in mind and are resilient against potential vulnerabilities. The CRA applies to manufacturers and developers of digital products rather than focusing on the internal cybersecurity practices of organisations.
The CRA complements NIS 2 by focusing on the security of digital products and IoT devices rather than organisational cybersecurity frameworks. While NIS 2 establishes cybersecurity standards for organisations providing essential services, the CRA ensures that the digital products they use or offer are secure by design.
Of course, this list is not, in any case, exhaustive. A few honourable mentions include:
So, regardless of whether your organisation falls directly under NIS 2 or not, you will definitely benefit from taking a proactive approach towards security – beyond only from a regulation standpoint.
NIS 2 not only raises the bar for cybersecurity across the EU for larger players, especially those providing essential or important services, but also, albeit indirectly, puts pressure on smaller organisations to improve their cybersecurity practices.
It is a good approach to think of security compliance not just as about meeting regulatory requirements but as an opportunity to strengthen your organisation’s resilience, protect critical assets, and build a more secure digital future.
Even smaller companies not directly affected by NIS 2 could benefit greatly from establishing and maintaining comprehensive and actionable security policies such as incident detection and response, supply chain security, access controls, and data backup management. Revising standard operating procedures, especially incident reporting protocols, will improve your cybersecurity maturity by helping you minimise damage in the event of a cybersecurity breach, even outside of meeting regulatory requirements.
For those wondering where to start with NIS 2 in particular, we recommend that you first assess whether and how NIS 2 impacts you. This will also involve identifying which subsidiaries or units may be affected. Also, get familiar with your local (or all relevant) transpositions of NIS 2, as each member state may introduce additional country-specific obligations, as well as compliance support, including training or vouchers, workshops, and projects. Beyond all – stay proactive and connected with local communities.
By adopting a proactive and curious approach to security, you will not only increase flexibility in meeting future regulatory requirements but also unlock new business opportunities. This mindset will enable you to navigate the evolving cybersecurity landscape more smoothly and contribute to a safer digital ecosystem—whether under NIS 2 or future regulations.